目的
本文详细介绍了在centos7上安装最新版openldap的过程和常见场景。
环境
操作系统:centos7.6
软件版本:openldap-2.4.44
配置示例: dc=example,dc=com
准备工作
为了方便配置防火墙以及禁用selinux,或者关闭防火墙。
查看防火墙状态
1 | firewall-cmd --state |
停止firewall
1 | systemctl stop firewalld.service |
禁止firewall开机启动
1 | systemctl disable firewalld.service |
关闭selinux
进入到/etc/selinux/config文件
1 | vim /etc/selinux/config |
OpenLDAP服务端配置
创建一个配置目录,将相关配置文件放在这个目录下面
1 | openldap |
安装LDAP组件并启动服务
1 | # yum安装 |
配置OpenLDAP服务
1 | # 生成Ldap root密码 |
ldap客户端配置
1 | # 安装组件 |
配置LDAP使用公钥(publicKey)远程ssh登录客户主机
openldap服务端配置
1 | # 安装openssh-ldap |
客户主机配置
1 | # 安装 |
登录验证
1 | ssh -i ~/.ssh/id_rsa 800001@10.116.72.15 |
配置LDAP账户可以登录的主机列表
测试使用的远程ssh服务器是10.116.72.15,我们验证如下
添加账户主机列表(host属性)不包含116.116.72.15 测试是否可以正常登录
添加账户主机列表(host属性)包含116.116.72.15 测试是否可以正常登录
需要通过Ldap远程登录的客户机配置
1 | vi /etc/nsswitch.conf |
备注:如果远程主机是centos6,配置稍有不同
1 | vi /etc/pam_ldap.conf |
LDAP账户配置
ldap命令或者ldapadmin管理工具为账户添加属性host,这个属性可以添加多次。
- 第一次配置不包含测试主机10.116.72.15
1 | ldapsearch -x uid=800001 -b 'ou=People,dc=example,dc=com' |
- 第二次配置包含测试主机10.116.72.15
1 | ldapsearch -x uid=800001 -b 'ou=People,dc=example,dc=com' |
以上,测试通过。
配置LDAP sudo权限管理
服务配置
CentOS7.6下安装的OpenLDAP是2.4.44 ,schema目录下并没有sudo.ldif以及sudo.schema文件,需要单独处理。 sudo是默认安装的,sudo相关目录下有sudo.schema模板文件schema.OpenLDAP
1 | find / -name schema.OpenLDAP -exec cp {} /etc/openldap/schema/sudo.schema \; |
权限配置
1 | vim SUODers.ldif |
将上面的demo(800001)账户配置为sudo权限
这里配置一个运维sudo role,名称为sudo_ops_role,简单配置为sudo 到root所有权限,并将800001加入该role
1 | vim sudo_ops_role.ldif |
客户端增加如下配置
1 | vim /etc/nsswitch.conf |
测试
1 | # ssh 800001@10.116.72.15 |
基于web的OpenLDAP管理工具phpldapadmin
实例在openldap安装,实际使用中可以部署在其他服务器上通过网络访问。前端还可以配置一个nginx去代理实现高可用
安装配置phpldapadmin
1 | # 安装组件 |
使用phpldapadmin
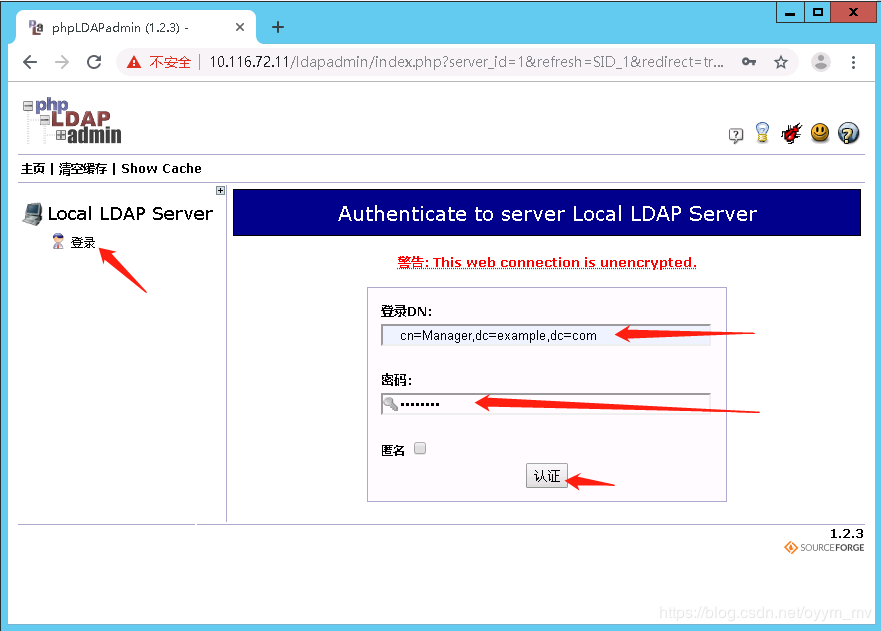
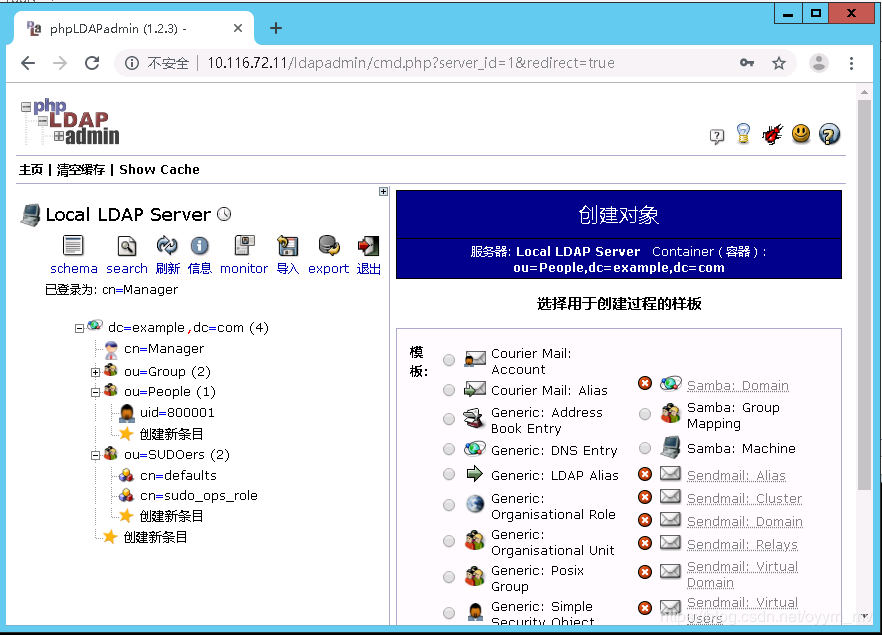
备注,如果报错如下
1 | Forbidden |
为phpldapadmin添加suorole配置模版
从官网地址 可以获取到sudoRole模板,可以在这个基础上进行修改
1 | ll /usr/share/phpldapadmin/templates |
vim /usr/share/phpldapadmin/templates/creation/sudo.xml 注意根据需要进行修改,我的sudo ou名称是SUDOers
1 |
|
vim /usr/share/phpldapadmin/templates/modification/sudo.xml
1 |
|
重启httpd服务
1 | systemctl restart httpd |
浏览器查看(ou=SUODers,dc=example,dc=com 创建一条子目录 sudoRole)
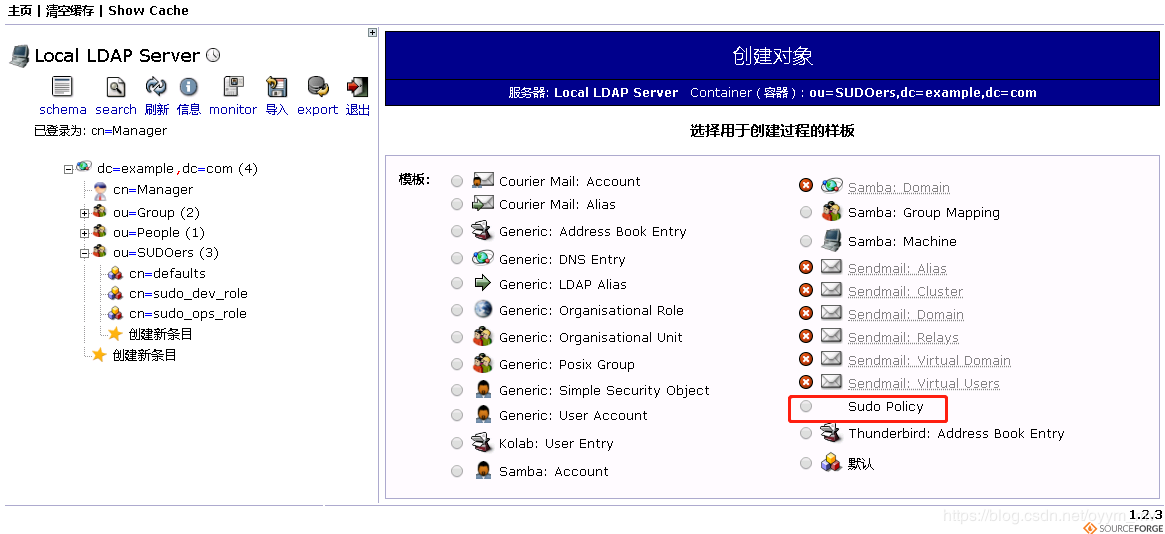
windows下的一个OpenLDAP管理工具 LdapAdmin
下载地址 LdapAdmin, 当前最新版本是1.8.3。 下载后直接解压就是一个exe文件。
创建连接到openldap服务
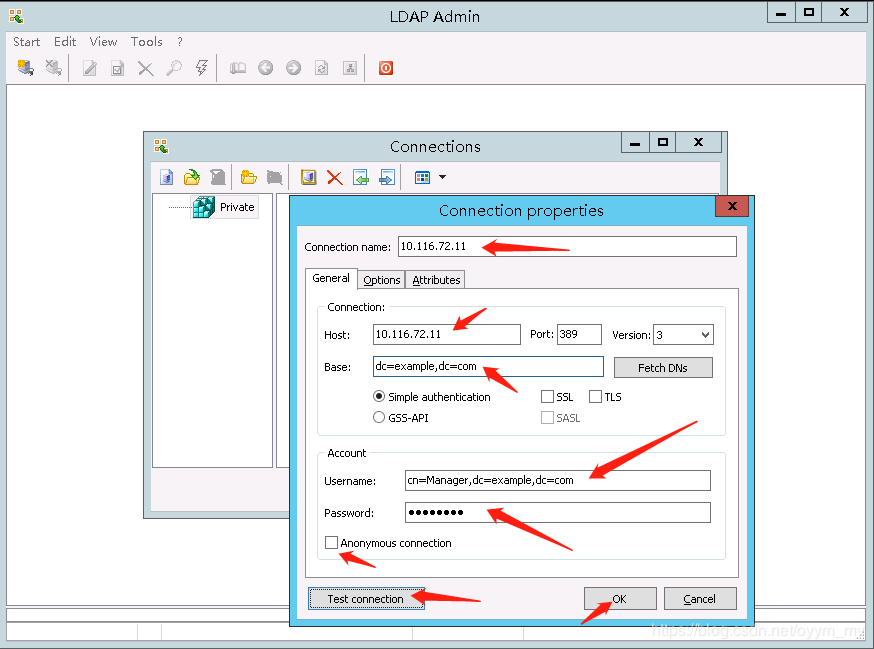
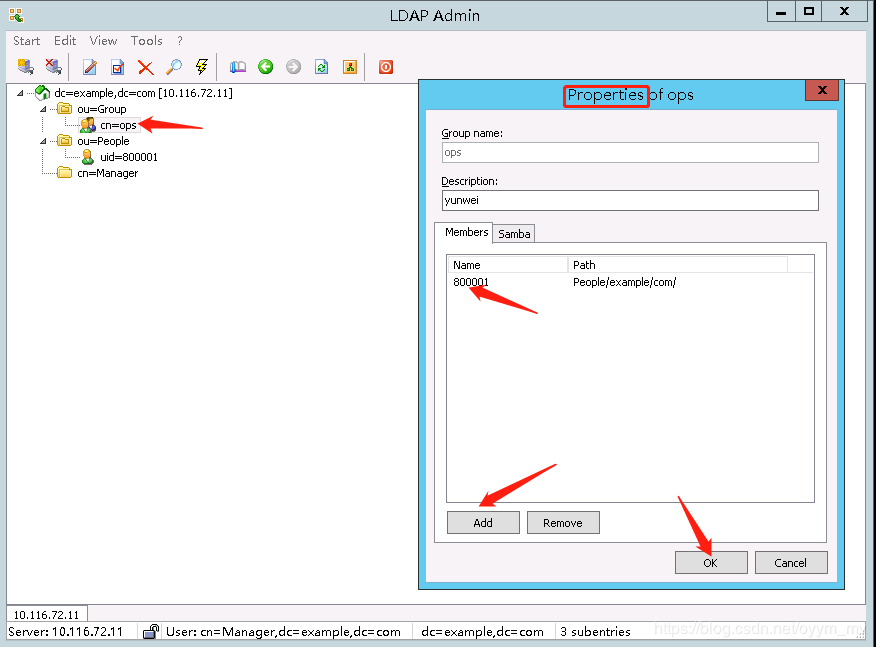
配置一个运维组ops,然后将用户800001加入到ops组
开启memberOf
默认情况下openldap的用户组属性是Posixgroup,Posixgroup用户组属性和用户没有实际的对应关系。如果要对应起来的话,就需要单独把用户设置到Posixgroup中
开启memberOf之后可以配置groupOfUniqueNames用户组属性,可以根据用户组过滤用户,这个过滤是唯一的
开启memberof,并让新增用户支持memberof
创建 memberof_config.ldif
1 | dn: cn=module{0},cn=config |
创建 refint1.ldif
1 | dn: cn=module{0},cn=config |
创建 refint2.ldif
1 | dn: olcOverlay=refint,olcDatabase={2}hdb,cn=config |
导入配置
1 | ldapadd -Q -Y EXTERNAL -H ldapi:/// -f memberof_config.ldif |
验证一下配置,这个命令可以列出所有配置
1 | slapcat -b cn=config |
禁止匿名访问
默认情况下匿名用户可以获取所有用户信息,甚至是密码字段,虽然密码字段是经过加密的那也很危险
创建disable_anon.ldif文件
1 | dn: cn=config |
导入配置
1 | ldapadd -Q -Y EXTERNAL -H ldapi:/// -f disable_anon.ldif |
设置ACL
拒绝所有用户查看用户信息,并且添加有ldap管理账号
创建acl.ldif
1 | dn: olcDatabase={2}hdb,cn=config |
导入配置
1 | ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f acl.ldif |
删除ACL
创建文件del_acl.ldif
1 | dn: olcDatabase={2}hdb,cn=config |
导入配置
1 | ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f acl.ldif |
创建管理用户
创建add_ou.ldif
1 | dn: ou=manage,dc=example,dc=com |
创建add_manage_user.ldif
1 | n: cn=ldapadmin,ou=manage,dc=example,dc=com |
导入配置
1 | ldapadd -x -D cn=root,dc=example,dc=com -W -f add_ou.ldif |

